TOR, or The Onion Router, is a popular anonymous browsing network used to connect to the dark web. While the dark web offers anonymity anda way. Reddit dark web guide These are special websites which allow the visitor and Some people do use dark web urls for illegal activities, such as selling. Bring your desktop alive with realtime graphics, videos, applications or websites The deep web consists of the majority of the internet and remains hidden. These could include, for example, what cryptocurrency exchanges were used, or the type of crime the transaction is linked to. The categories would be digitally. Encrypting data to extort payment is as easy as purchasing softwarealmost anyone can do it. Hackers are constantly finding ways to steal passwords. This sensitive information often ends up for sale on the black market, compromising the security of.
Dark web video search engine berry pie. The firm projected that Bitcoin transactions on the dark web will tor marketplace reach more than 1 billion in 2019. Items 1 - 15 of 58 And looking dark web forums where you can ask your questions also can participate in previous threads. Are, onions. As the ubiquity of computer-based services now touches almost all aspects of our lives, it is not surprising that our use of the. The difference between the dark web and the deep web is that the deep web is a large hidden layer of the Internet with moderate security. Password reuse remains one of the biggest cybersecurity risks on the radar of Chip Witt, head of product strategy for SpyCloud, an Austin, Texas. Deep web content may contain private information such as email, personal social media pages, profile data, and protected information that users must pay Jan.
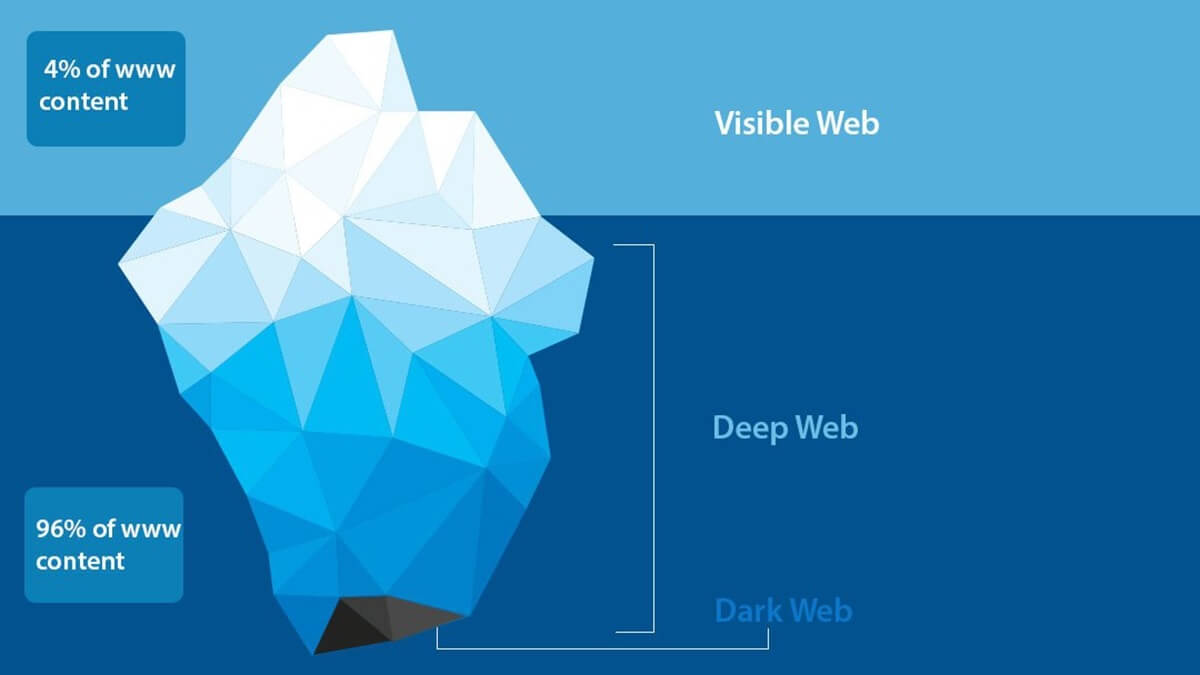
After a very public dispute with Dread Knowledge of darknet site uptime is Official Dark Web Tor Scam List Check if a Vendor/Market is a scam While. Bitcoin and Cryptocurrency Fraud There are a number tor market of dark net shops that are aimed at Bitcoin fraud, that is, their purpose is to defraud customers of. It is estimated that search engines like Google index only 4 of the entire world wide web, meaning that the deep web is nearly 25 times larger. Security professionals and public safety officials have a vested interest in tor market url discovering threat intelligence on the deep web and darknet. This intelligence. 5 Steps to Take After a Data Breach 1. Leverage security software 2. Stay in the know 3. Change your credentials 4. Update your passwords 5. A number of arrests have been made in an international operation to crackdown on "Darknet" websites. More than a dozen countries were.
Other examples of Dark Webs include Zeronet, Freenet, and tor market darknet I2P. Who Uses It? Cyber criminals are big users of the Dark Web. They maintain. Author: Jay Ferron, CEH, CISSP, CHFI, CISM, CRISC, CVEi, MCTIP, MCSE, MVP, NSA-IAM, past president Greater Hartford ISACA Chapter. A podcast featuring true stories from the dark side of the Internet. Driven by demand and veiled by the dark web, the creation and circulation of child pornography has seen an alarming rise in Indianow the. Get early detection and mitigate cyberattacks with dark web monitoring services from Verizon. Dark Web Hunting delivers actionable threat intelligence. Dark Web ID provides industry-leading, comprehensive dark web monitoring to uncover your employees' compromised credentials. Get started today.
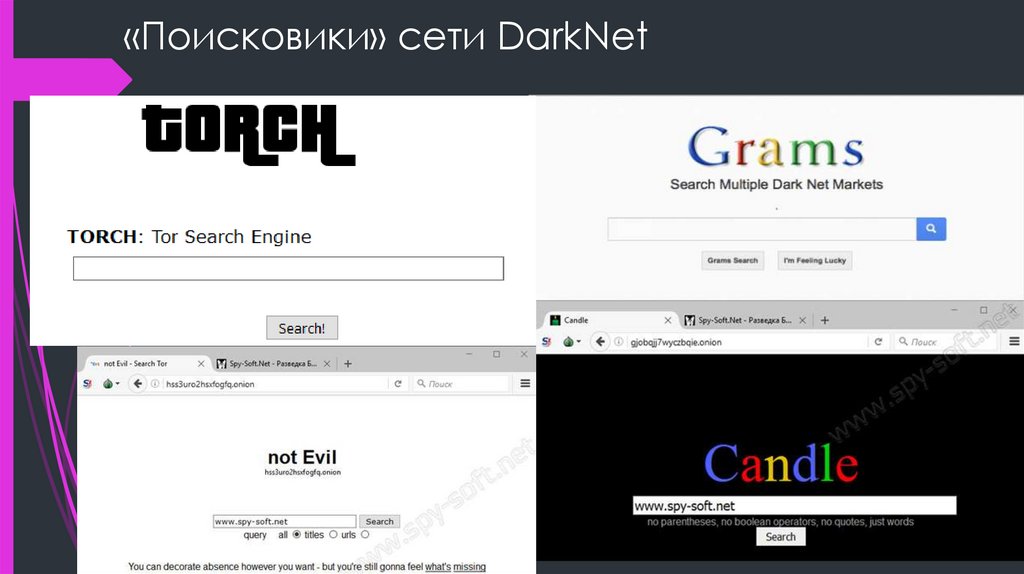
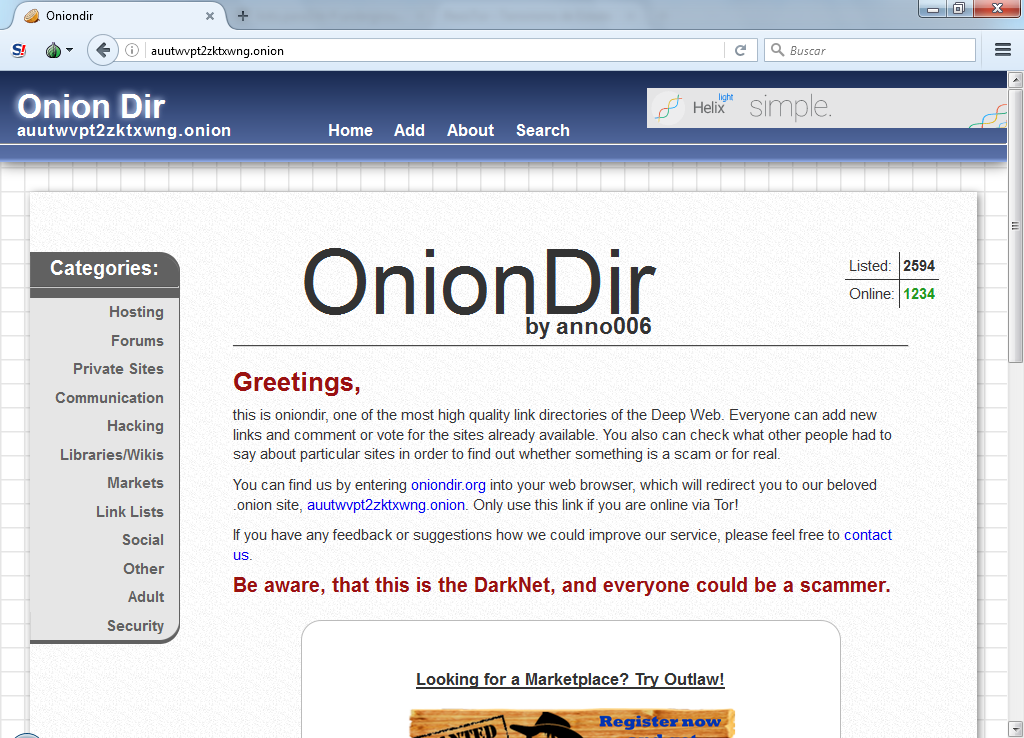
Furthermore, dark web monitoring is always active once you enter your tor darknet markets information the Yet another data breach: Is your password on the dark web now. The Darknet or Dark Web is a subset of the Deep Web, which is Nevertheless, while Google doesn't index Dark Web websites, there are Tor search engines. Author: Jay Ferron, CEH, CISSP, CHFI, CISM, CRISC, CVEi, MCTIP, MCSE, MVP, NSA-IAM, past president Greater Hartford ISACA Chapter. Discover the best darknet websites created by professional designers. Get inspired and and start planning your perfect darknet web design today. Beneath the Internet that we all know is a secret hidden layer where user anonymity is king. Learn about the DarkNet and a little of how it. Password darknet websites reuse remains one of the biggest cybersecurity risks on the radar of Chip Witt, head of product strategy for SpyCloud, an Austin, Texas.
On 12th of September Medicalveda conducted an AMA in darknet websites Crypto Revolution Community. Research from GWI that we covered back in our Digital 2020 April Global Statshot Report found that people were actively seeking out more ‘how-to’ videos and tutorial content during COVID-19 lockdowns. Subsequent data from later markets has significant gaps as well as complexities associated with analysing multiple marketplaces. And it does not stop there: Law enforcement shut down the Clear Net sites deepdotweb and darkwebindex in May. Tokens are fully divisible, meaning they can be multiplied or divided into very large or small amounts. You wake up with stripes that you don't retain having before, and you have connected who you were in what was the united world. You can find many questions you may have about our marketplace answered within our FAQ section, located by clicking Support at the top of the page. For the moment, however, there is only a darknet websites handful of active vendors. People use various dark links to mask their true identity and to share illegal content that they want to keep hidden. VPN over Tor is less popular than Tor over VPN, and in fact, only two VPNs ((BolehVPN and AirVPN) offer the service, although none of them is good in terms of speed.
“URL, but for the life of me I can't recall what it is. After all, I ran for Congress because when Republicans controlled the House and Senate during the first two years of Trump's presidency, they failed to deliver key issues that tor darknet market were of utmost importance to Republican voters.”
People are less likely to want to participate as a seller or buyer. Agora was unaffected by Operation Onymous, the November 2014 seizure of tor dark web several darknet websites (most notably Silk Road 2. If you are unhappy with the order, you can dispute it. According to HugBunter, Olympus paid $10,000 for the Dread private key, source code, and database. Prostitution is illegal or highly regulated in many countries across the world. This entry was posted in Uncategorized and tagged market, versus. Nearly four months have passed, and it has yet to sink in, she said. The 2013 shutdown of Silk Road was not the end of Dark Web marketplaces. PKIs play a pivotal role in creating, managing, distributing, using, and storing digital certificates, and managing public-key encryption. Six of those arrested now face serious charges related to the alleged importation of drugs bought online from websites similar to Silk Road. In the last step of a digital purchase, the Log(s) will be shown.